hardware
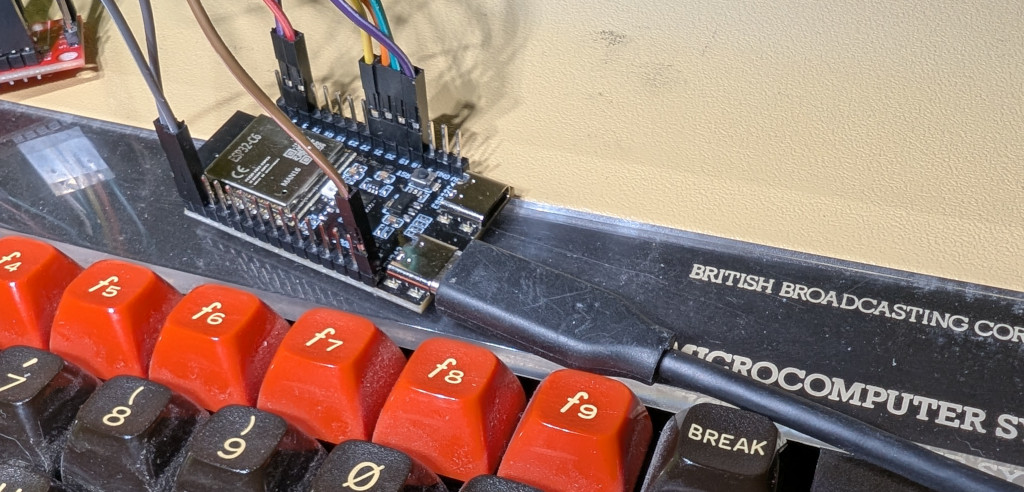
Bridging Centuries: Econet Meets Wi-Fi
*NET with ESP-32

hardware
*NET with ESP-32
hardware
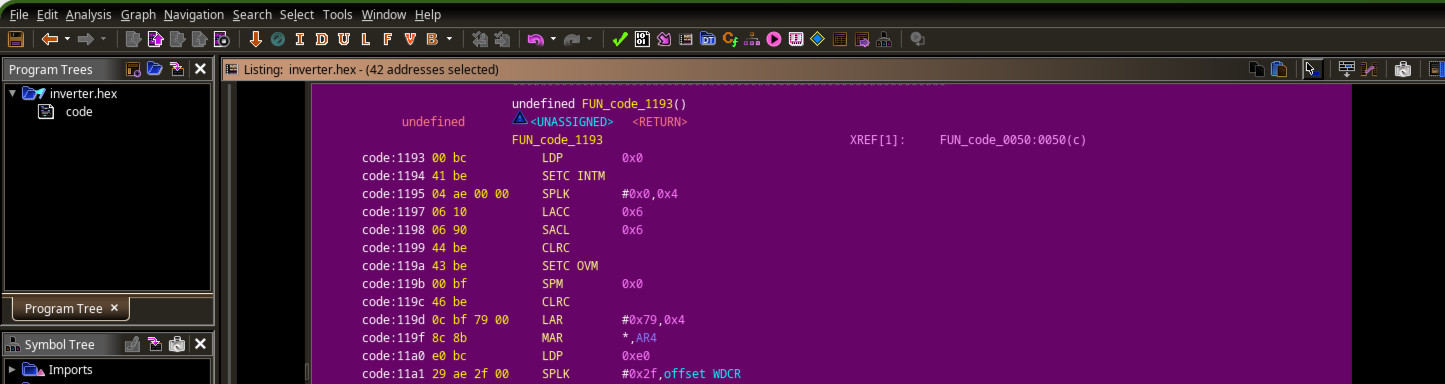
PVI-xxx Inverter DSP firmware extraction and reveng - A look at the brains of a Grid-Tie inverter.
hardware
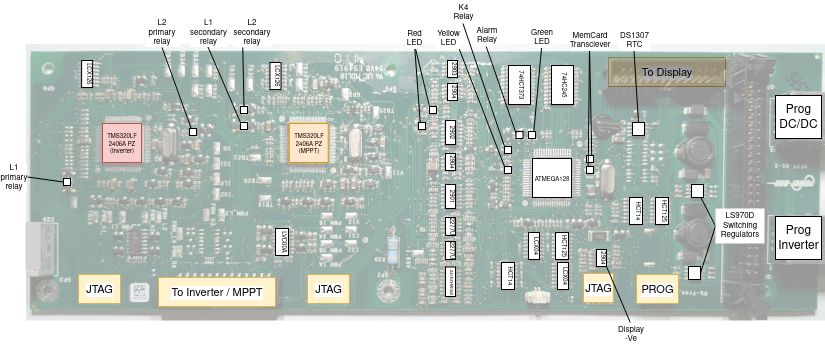
PVI-xxx Inverter Deep Dive - A look at the brains of a Grid-Tie inverter.

hardware
PVI-xxx Inverter Teardown - What’s Inside, What Fails, and How to Fix It

hack
Liberating your EtekCity ESF24 Fitness scale from the cloud

hack
Liberating your Silvercrest (Lidl) Smart Home Gateway from the cloud
ukpaye
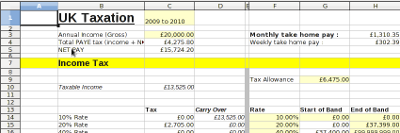
Free tax calculation spreadsheets for UK tax including PAYE, income, NI, corporation tax, dividends and official 2017/2018 rates.
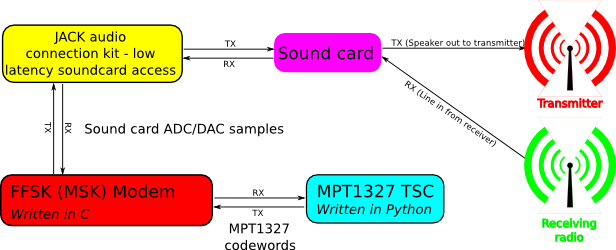
radio
An open source, software implementation of an MPT1327 Trunking System Controller (TSC).
radio
An open source, software implementation of a GM1200 control library with SB9600 / SBEP.

flight
A spreadsheet for assistance with VFR flight planning